Gmail spam filter now biting itself
Gmail is getting more ridiculous than ever. It now identifies google’s own emails as spam. Previously I would get annoyed about my bank’s or shopping site’s emails buried in the spam folder, but now I’m in peace with the thing – it is just stupid piece of AI, nothing hostile like we’re accustomed to thing of Google.
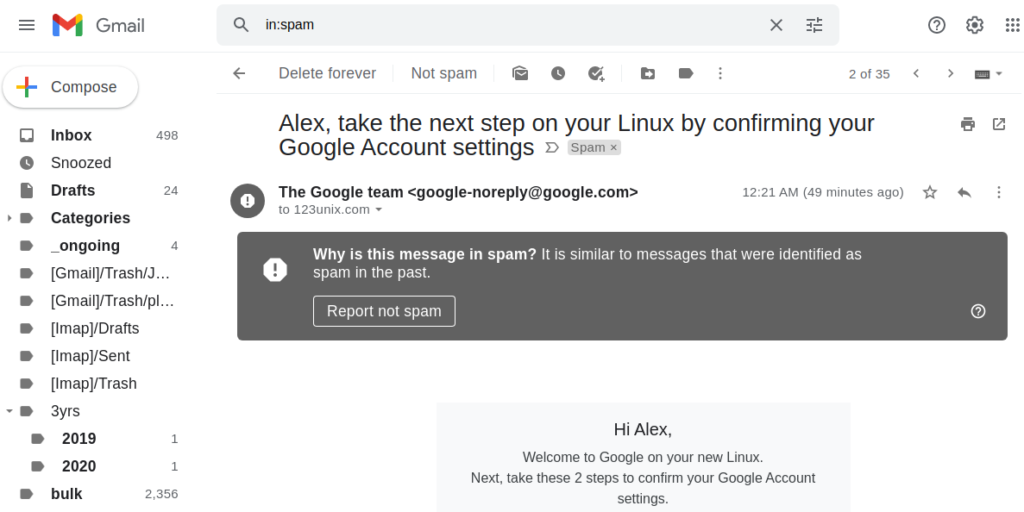
If you think this was some non-important type of email I could bring up another example from the same haul – that one was a notification from Google about me changing my payment method in Google AdSense – similarly got trapped in spam.